Blogs
Six crucial questions for real-time data readiness

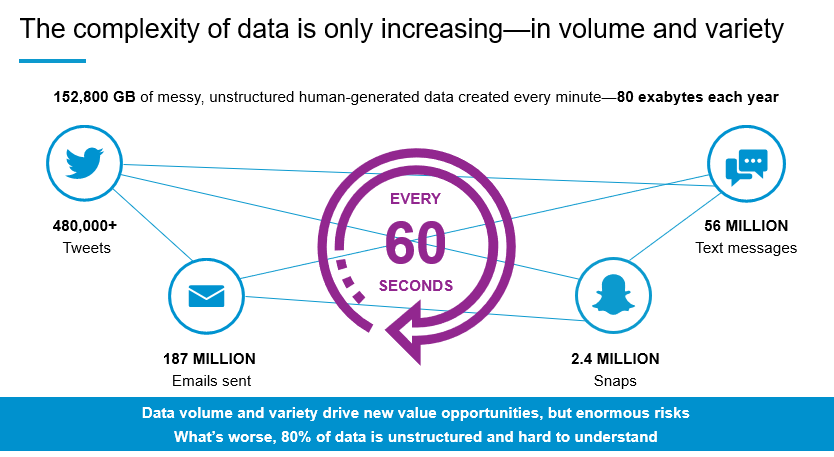
The typical company has generated a bigger digital footprint in the last two years than in all its previous years of existence. In fact, 90% of all data has been created within the last two years, and we are heading toward creating 40 zettabytes (with a z) of data this year. We know you've likely seen the infographics and stats, but these numbers bear repeating because they provide context for the burden that companies shoulder as they struggle with data management: wasted time, increased costs, risks associated with non-compliance—not to mention the frustration of having to deal with all of these factors.
ASK THE RIGHT QUESTIONS
What steps can you take to better meet process, security, and compliance demands in your organization? How can you get a handle on your data so you can take the needed steps to support and protect your business?
It all starts with monitoring and management of your data as it’s produced, so nothing gets lost, wrongly organized, or worse, breached. Take a moment to answer these six questions for a quick gauge of your company's real-time data readiness and response.
Fast And Targeted
Can your organization remotely access any endpoint and go directly to the data or area(s) of concern, without being overwhelmed with data volumes or complexity?
The Bigger Picture
Can your organization explore activity across endpoints and correlate it with activity residing only in memory, on the network, or any other network-based human-generated artifact?
Detect & Prevent
Can your organization identify malicious behavior, follow through on any tactics, techniques, and procedures (TTPs), collect the data to develop indicators of compromise (IOCs), and intercept the problem before it matters?
Real Value ROI
The upfront investment is unavoidable, and ROI is challenging to quantify, but can your organization reasonably and accurately provide a fixed and variable cost analysis—from decreasing data storage of duplicate/unnecessary data to the actual business value of successfully blocking a threat?
Give Traditional Forensics Its Place
Does your organization still employ traditional, time-tested forensics for in-depth insight into what activities took place, ideas on how to counteract it in the future, and winning insights into developing a robust and defensible case?
Educate Proactively
Does your organization leverage lessons learned to roll out education programs, improve your security, and reduce your risk for both threats and non-compliance?
REAL-TIME READY, NOW WHAT?
Did you answer a resounding “YES!” to each of those six crucial questions?
If only it were that easy. We know data monitoring and management for the purposes of threat handling and maintaining compliance is very often a work in progress; however, once you get there, the payoff comes in the form of improved and positive outcomes for the organization:
- Compressed response times. From responding to discovery or privacy requests to acting on internal or external security threats, reaction time improves when data is centralized, classified, and highly searchable (the perfect job description for an indexed data lake).
- Accelerated incident resolution. Governed data is data with fewer surprises and more transparency. It allows you to sort through evidence more quickly, gets to the facts faster, and jumpstart the investigation of an incident that has occurred.
- Reduced risk. When your governance program enables you to find and remove unauthorized or unsecured copies of sensitive data, you reduce the risk of insider abuse and other malicious breaches.
When you take steps to make all your organization’s data instantly visible, searchable, and able to be analyzed, you’re simultaneously making major strides toward governance and compliance.
TAKE BACK CONTROL
Your organization needs to take back control of your data by indexing what you have and uncovering relevant key information that uncovers compliance risks, improves investigations, and increases knowledge and decision-making.
Be the data hero for your organization. There's no better time than the present to start implementing better data management practices for an improved security and response posture—including a single software process that enables total enterprise collaboration from governance to endpoint security and all the way through investigation and litigation.
Contact us to find out how Nuix will support your needs.










